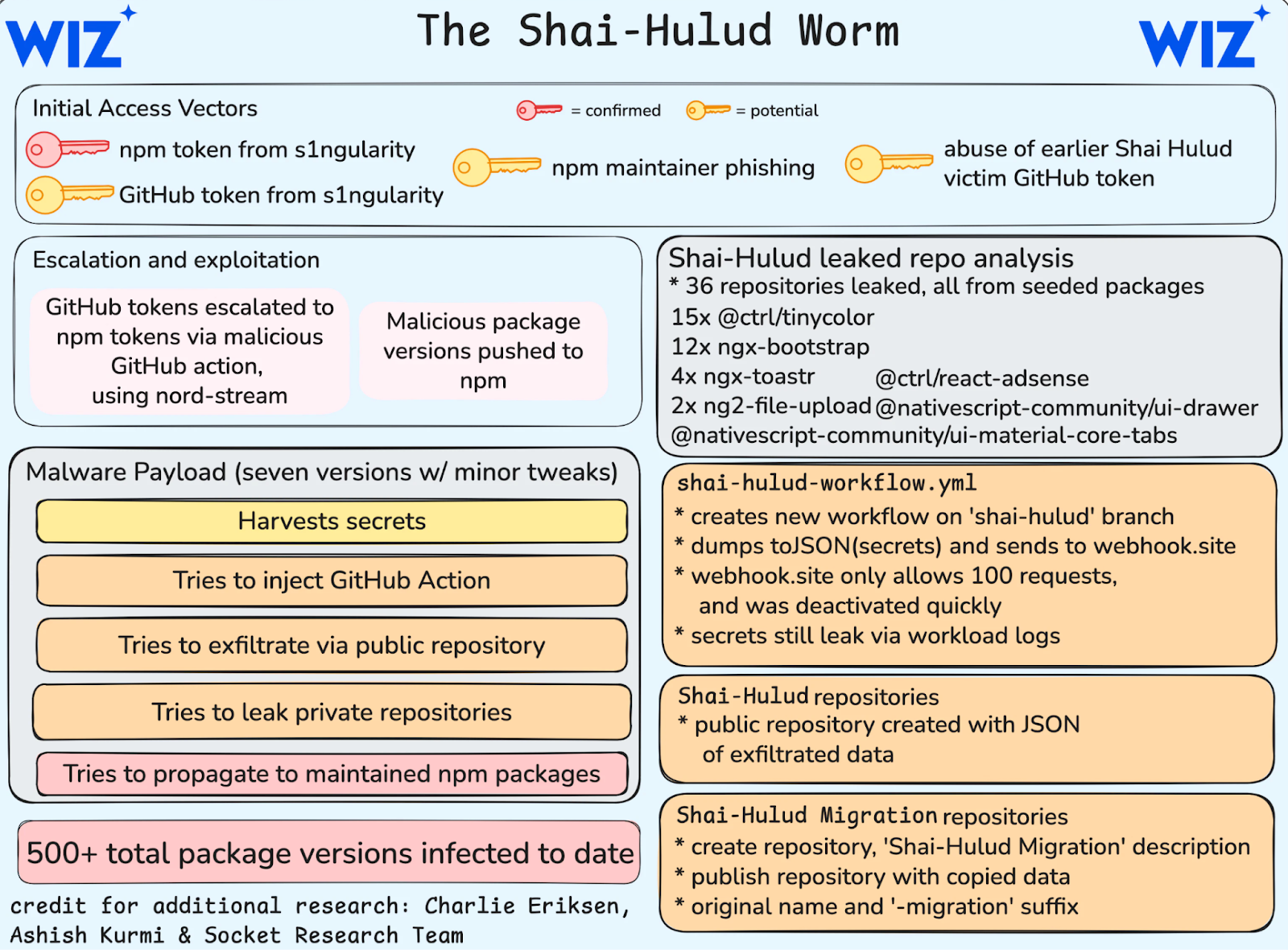
On September 8, 2025, developer "qix" received a seemingly routine security email from "npm support." The message looked legitimate - urgent language about account security, official-looking headers, a believable sender address. Within hours, this single phishing email had compromised 18 of the most trusted packages in the JavaScript ecosystem.
But this wasn't just another supply chain attack. The malicious code specifically targeted Web3 wallets, designed to steal cryptocurrency by silently rewriting transactions before users could sign them.
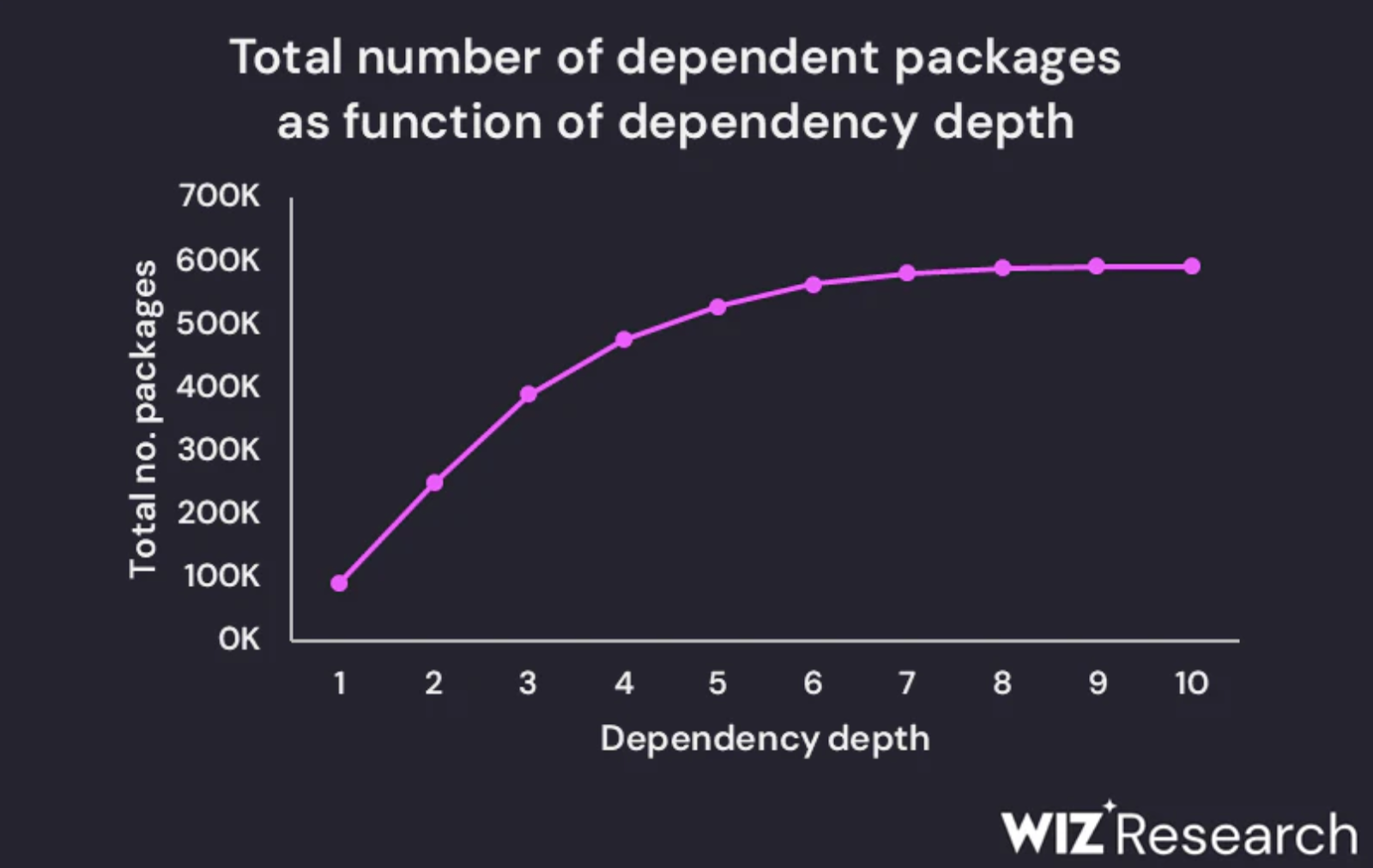
By the time the community caught on, the malware had already infiltrated systems with 2.6 billion weekly downloads, making it one of the largest supply chain attacks in history.

What happened in those critical hours
13:16 UTC: Malicious versions of chalk, debug, and 16 other packages go live on npm
~15:20 UTC: Community spots suspicious behavior in GitHub issues and social media
16:00 UTC: npm security revokes access and yanks malicious versions
Exposure window: 2 hours and 44 minutes of active threat
The targeted packages weren't obscure libraries. They were fundamental building blocks of the JavaScript ecosystem:
- chalk (terminal string styling) - used by virtually every Node.js project
- debug (debugging utility) - embedded in countless applications
- strip-ansi (ANSI code removal) - a basic text processing tool
The attack succeeded because these packages are so trusted and ubiquitous that developers install them without question.
The crypto-specific payload
Traditional supply chain attacks steal credentials or install backdoors. This attack was different - it was a specialized cryptocurrency drainer distributed through the most trusted channels in web development.
The malicious code:
- Monitored Web3 wallet interactions in real-time
- Intercepted transaction signing across multiple chains (ETH, BTC, SOL, TRX)
- Replaced recipient addresses using fuzzy matching algorithms
- Remained dormant until users initiated crypto transactions
The attackers understood Web3 deeply. The malware hooked into window.ethereum for MetaMask interactions, Solana wallet APIs, and even used legitimate-looking CloudFlare headers to hide data exfiltration.
The Solana ecosystem gets hit again
This wasn't an isolated incident. Just months earlier, in December 2024, the Solana ecosystem faced its own devastating supply chain attack.
The @solana/web3.js compromise:
- Target: The core JavaScript library for Solana development (450K+ weekly downloads)
- Attack window: December 2, 2024, 3:20 PM - 8:25 PM UTC (5 hours)
- Method: Phishing attack on package maintainer
- Damage: $164,100 stolen (674.86 SOL)
The attackers added an addToQueue backdoor function that captured private keys during transaction signing. Every time a developer's application signed a Solana transaction, the private key was silently sent to the attacker's server.
What makes Solana attacks particularly dangerous is that many Web3 projects handle private keys directly in their applications, unlike Bitcoin or Ethereum where wallet software typically manages keys. This creates more opportunities for supply chain attacks to capture signing material.
Why Web3 is a prime target
Web3 projects face unique supply chain risks that traditional software doesn't encounter:
- Massive financial incentives: Successful crypto theft provides immediate, irreversible payouts worth millions. No need to monetize stolen data or set up complex fraud operations.
- Expanding attack surface: DeFi protocols typically integrate 50-200 dependencies, from UI libraries to blockchain SDKs. Each dependency can become an attack vector.
- Detection challenges: Malicious code targeting Web3 wallets often resembles legitimate blockchain interaction code, making it harder to spot in automated scans.
- Developer trust patterns: Web3 developers often prioritize speed and composability, sometimes skipping thorough security reviews of dependencies.
The mysterious patterns
Several aspects of recent supply chain attacks remain puzzling:
- Coordinated timing: The September 2025 npm attack and December 2024 Solana attack both used nearly identical phishing techniques. Same threat actors?
- Selective targeting: The September attack only activated in browser environments and specifically looked for crypto wallet interactions. Why not target all users?
- Quick discovery: Both attacks were discovered within hours by community members, not security tools. Were these meant to be caught quickly as proof-of-concept demonstrations?
- Limited exploitation: Despite massive reach, relatively few funds were actually stolen. This suggests either poor execution or these were tests for larger future attacks.
What traditional security misses
Most Web3 projects approach supply chain security using traditional software practices, creating critical blind spots:
- Static analysis gaps: Tools like npm audit catch known vulnerabilities but miss novel attack patterns designed for Web3 wallets.
- Build-time only checks: Security scanning happens during development but not at runtime when malicious code actually executes.
- Context blindness: Traditional tools can't distinguish between legitimate blockchain interactions and malicious wallet manipulation.
- Dependency trust: Teams monitor package updates but don't track maintainer changes or unusual release patterns that could signal compromise.
The Web3SecNews analysis highlights that most Web3 projects focus security efforts on smart contract audits while completely ignoring the development pipeline and dependency chain that delivers code to users.
The real-time monitoring necessity
The September attack was contained quickly because the community spotted suspicious behavior and npm responded rapidly. But most Web3 projects had zero visibility into whether they were actually affected.
What protocols need:
- Dependency health tracking: Real-time monitoring of third-party package security status and maintainer changes
- Runtime behavior analysis: Detection of unexpected wallet API calls or transaction modifications
- Supply chain threat intel: Early warnings when dependencies are compromised
- DevOps pipeline security: Monitoring build processes for supply chain infiltration
At Guardrail, we've built systems specifically for this problem. When the September attack happened, our customers received alerts within minutes, not hours. They could immediately identify affected systems with actionable steps offered to them and were able to take protective action before funds were at risk.
We’re building to monitor the complete software supply chain - dependency health, maintainer changes, runtime behavior, and build pipeline integrity - providing real-time alerts when something looks suspicious.
The defense playbook
The protocols that avoided both the September npm and December Solana attacks shared common practices:
- Dependency pinning: Used lockfiles that prevented automatic updates to compromised versions
- Staged deployments: Updates went through internal testing before production
- Runtime monitoring: Systems that could detect unusual application behavior in production
- Rapid response: When alerts came in, teams could quickly identify and isolate affected systems
But these practices only work if you know an attack is happening. Most protocols discovered the compromises hours later through community alerts..
Conclusion
Web3's supply chain problem isn't going away - it's accelerating.
Attackers have discovered that compromising trusted dependencies is more effective than trying to exploit individual protocols.
Guardrail provides comprehensive supply chain security for Web3 protocols, including dependency monitoring, runtime analysis, and DevOps pipeline security. We notified the September npm attack to our internal teams and helped customers respond before any funds were at risk.

.png)



