Timeline: 12:18 AM - vault deployed → 1:53 AM - $9.6M stolen → 2:53 AM - protocol emergency response
The attack started through a flash loan
Resupply is a stablecoin protocol backed by Collateralized Debt Positions, operating as a sub-DAO of Convex and Yearn Finance. On June 26, 2025, they deployed a new wstUSR market using ERC-4626 vault contracts, standardized tokenized vaults that represent shares of an underlying asset pool.
The attacker identified this newly deployed vault with virtually no liquidity and executed a flash loan attack, borrowing funds temporarily within a single transaction to manipulate the system.
Step-by-step details of the attack
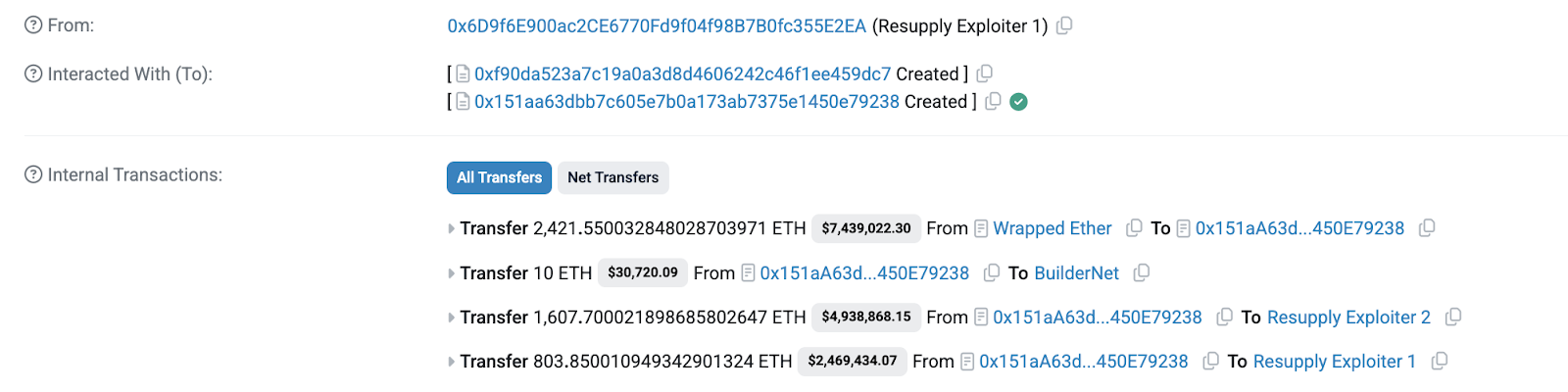
1. Flash loan setup
- Borrowed $4K USDC from Morpho
- Converted to 4K crvUSD for the attack
2. The donation manipulation
- Donated 2,000 crvUSD directly to the vault contract
- Deposited 2 crvUSD to mint 1 wei of cvcrvUSD shares
- Key insight: That single wei now represented the entire donated amount in the vault's accounting
3. The math calculation exploit
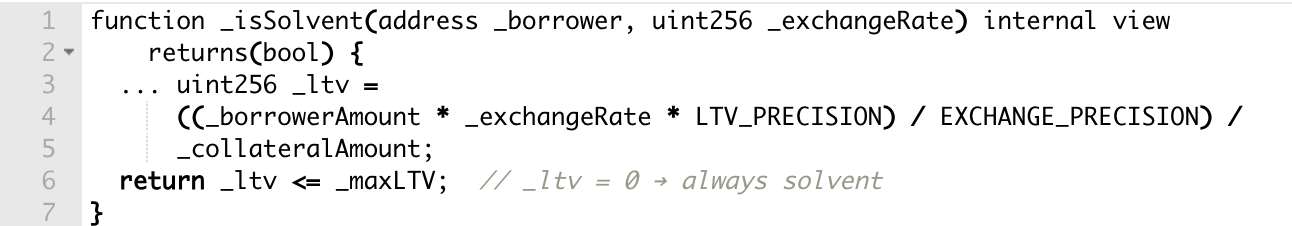
When calculating exchange rates, the protocol's getPrices function returned an inflated value of 2,000,000,000,000,000,001,998,001,998,001,998 for the 1 wei of collateral.
The exchange rate calculation divides 1e36 by this inflated value:
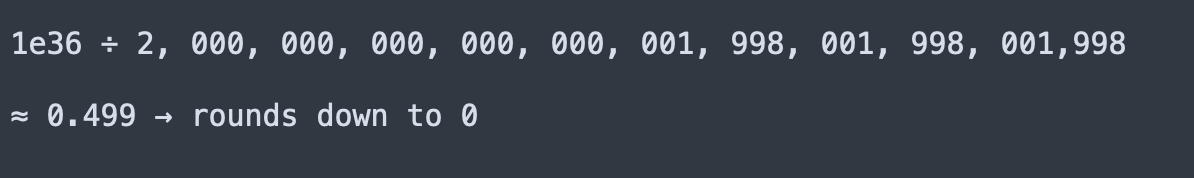
An exchange rate of zero = infinite borrowing power.
4. Drainage of funds
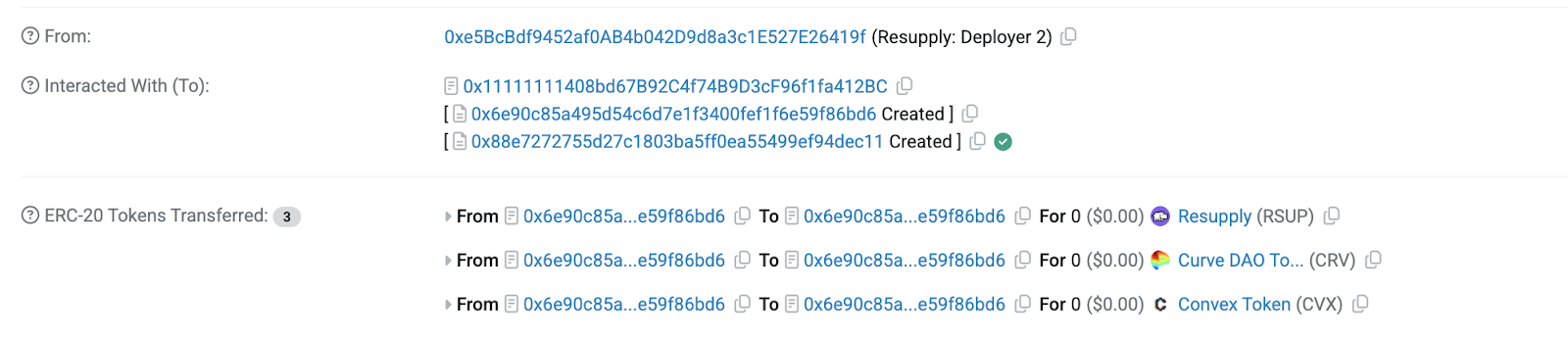
With 1 wei of worthless collateral, the attacker borrowed 10 million reUSD tokens - the protocol's entire borrow limit. The _isSolvent check passed because with a zero exchange rate, the loan-to-value ratio was zero.
5. Laundering of funds
- Swapped reUSD for stablecoins and ETH via Curve and Uniswap
- Split funds across multiple addresses
- Laundered through Tornado Cash
Why are empty vaults vulnerable?
ERC-4626 vaults calculate share prices using balanceOf functions. In empty vaults, small donations have outsized effects:
Normal vault: 1000 shares represent 1000 tokens = 1:1 ratio
Empty vault after donation: 1 share represents 2000 tokens = 1:2000 ratio
This inflated ratio breaks the protocol's price calculations, enabling the exploit.
The domino effect 🚨
🚨 reUSD depegged to $0.98 immediately.
🚨 Resupply's TVL plummeted as users lost confidence.
🚨 The protocol emergency response set borrow limits to zero.
Prevention is simple yet critical
This attack was 100% preventable:
1. Virtual shares/offsets
Implement virtual shares that act as a baseline, preventing empty vault manipulation. The vault pretends it already has assets and shares from deployment, making small donations irrelevant.
2. Proper vault initialization
Seed new vaults with initial liquidity to make donation attacks economically unfeasible. Even 1000 tokens would have prevented this exploit.
3. Exchange rate boundaries
Implement minimum exchange rate thresholds to prevent zero-value scenarios.
Detailed official write-up from the Resupply team on this incident, which includes more steps and specific details.
Key takeaways & preventive measures
- Never deploy empty ERC-4626 vaults without initialization
- Implement virtual shares for new vault deployments
- Use time-weighted averages for price calculations
- Build circuit breakers for unusual market conditions
- Avoid newly deployed protocols in their first hours
- Monitor vault initialization practices
- Diversify across multiple protocols
Conclusion
The Resupply hack demonstrates how a well-known vulnerability can still cause massive damage when proper safeguards aren't implemented.
A $4K flash loan became a $9.6M theft because of a missing initialization step. In DeFi, security isn't just about smart contract code - it's about understanding economic incentives and attack vectors that come with every deployment decision.
At Guardrail, we help protocols implement robust security practices from day one. Contact us to discuss protecting your protocol from common attack vectors.