The Gap: Attack begins → Hours before detection → $27M stolen vs. real-time alerts could have limited losses to under $1M.
BigONE exchange’s operational interactions with third-party services
BigONE is a cryptocurrency exchange handling millions in digital assets across multiple blockchains. Like most exchanges, they rely on hot wallets for daily operations and third-party vendors for various operational components.
On July 16, 2025, this trust in the supply chain became their biggest vulnerability.
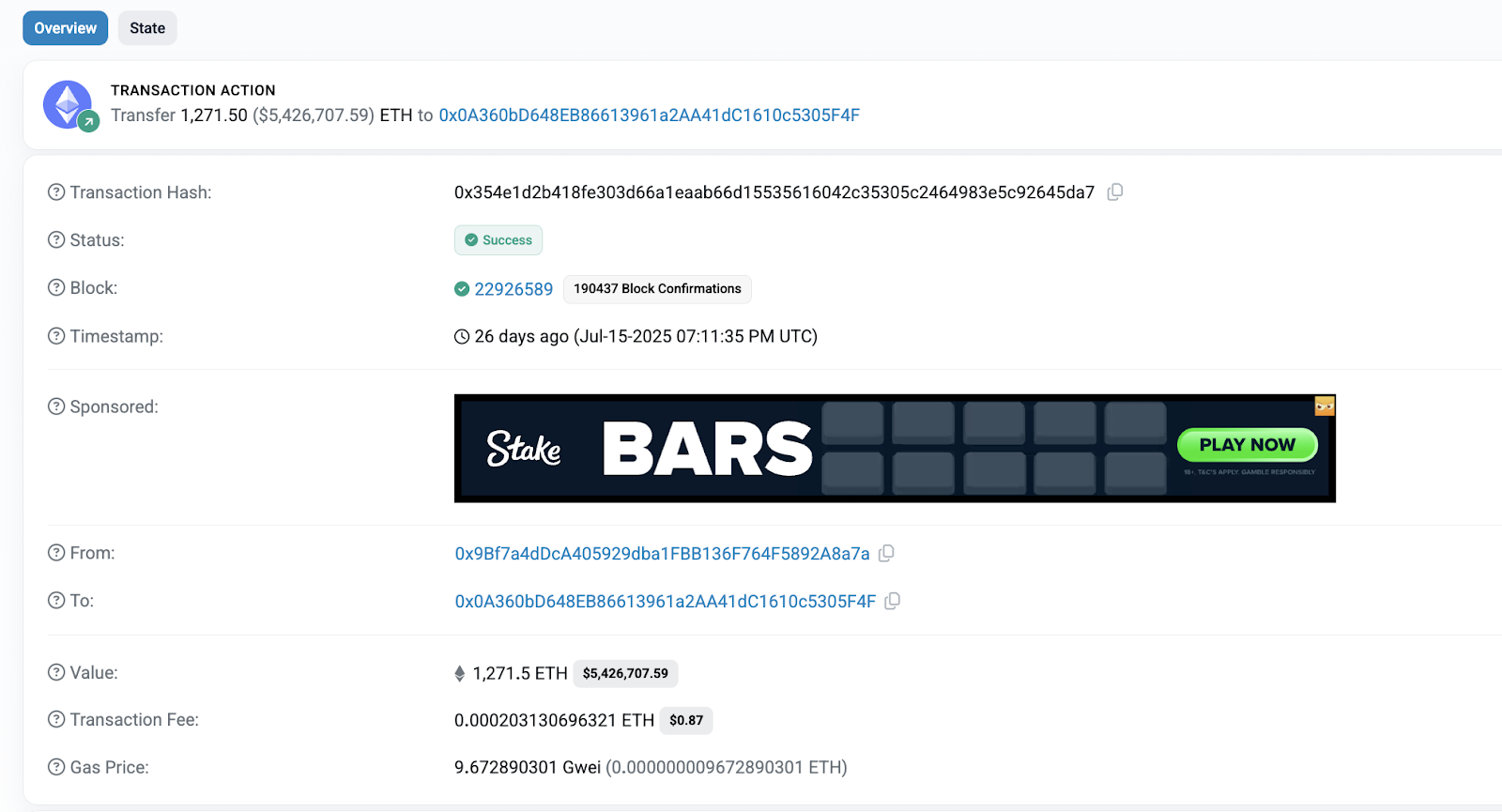
How did the attack happen?
Unlike typical exchange hacks targeting private keys or exploiting smart contract bugs, the BigONE attack was far more insidious. The attacker compromised third-party software that controlled hot wallet operational logic.
Instead of breaking the vault door, they convinced the vault's own security system to open it willingly.
Before we dive-in, let’s understand how the supply chain attacks work
Traditional exchange security practice:
- Attacker → Tries to break → Exchange defenses → Blocked
Now via the supply chain attack route:
- Attacker → Compromises vendor → Vendor updates → Exchange trusts → Backdoor installed
- The compromised third-party code altered the logic governing account-related servers, making unauthorized withdrawals appear legitimate to internal systems.
Many chains got affected due to this internally
Once the attacker was inside, they systematically drained funds across multiple networks:
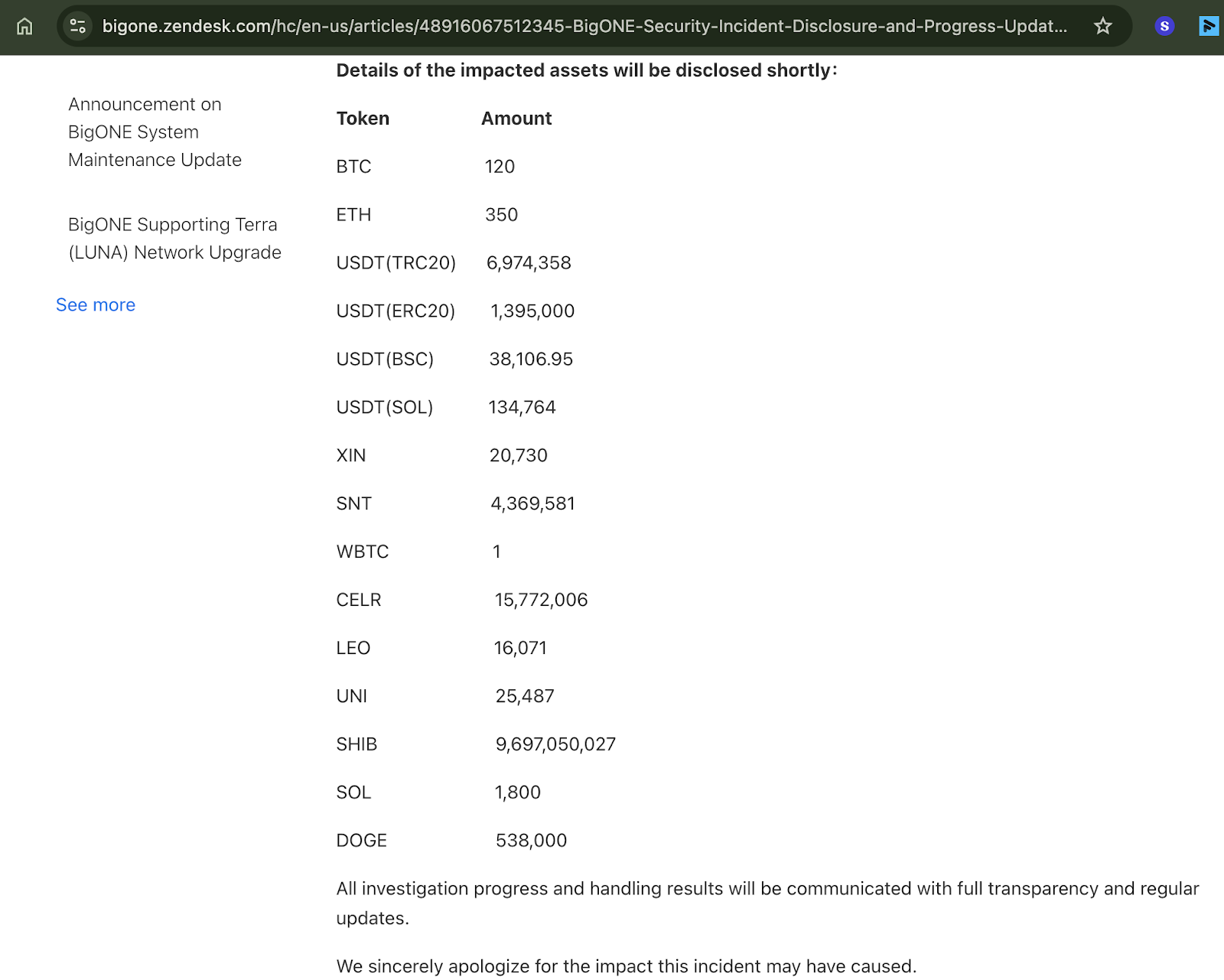
Total damage: $27 million across the Ethereum, Solana, TRON, and Bitcoin blockchains.
How having real-time monitoring could have changed everything
Alert #1: Unusual asset movement pattern (early-detection)
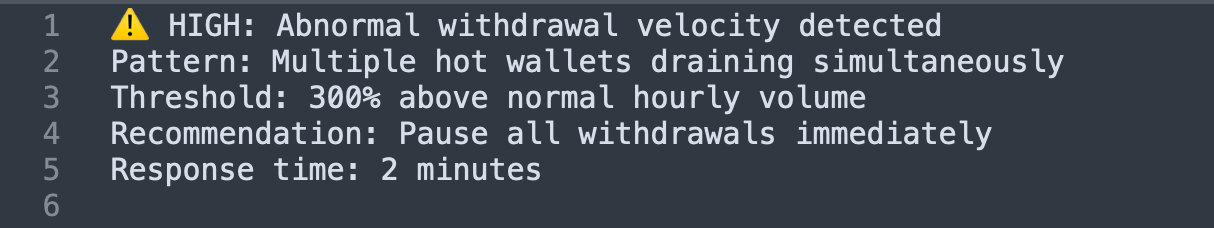
Alert #2: Cross-chain co-ordination (red-flag)
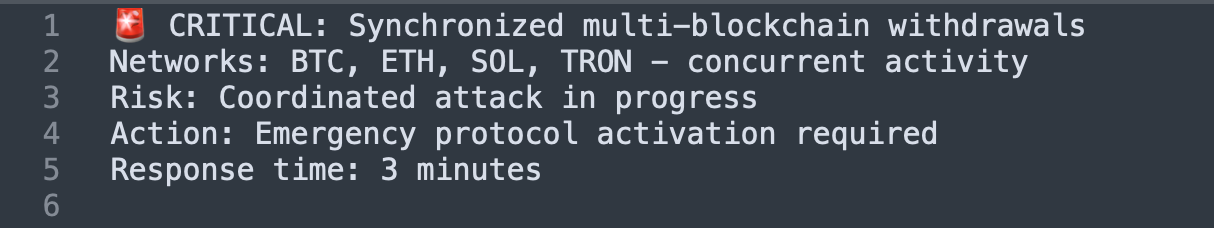
Alert #3: Behavioral anomaly in system logic
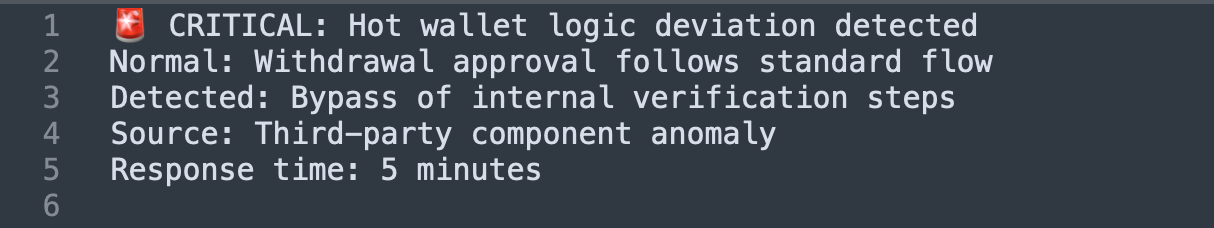
So in short, this is what actually happened...
❌ Hours of undetected drainage before internal alarms
❌ $27M stolen while systems appeared normal
❌ No real-time vendor monitoring
❌ Attack discovered through volume thresholds, not behavioral analysis
If having a real-time monitoring solution, this scenario could be different:
✅ < 2-minute alerts on unusual withdrawal patterns
✅ Cross-chain correlation detection in minutes
✅ Third-party component monitoring
✅ Losses limited to <$1M through rapid response
The swift evolution of the threat landscape in 2025 lends significant weight to the implications of this attack.
BigONE's hack adds to a record-breaking year for crypto crime:
- $2.17 billion stolen in 2025 - already surpassing all of 2024
- Supply chain attacks increasing as direct exploits become harder
- Individual wallet thefts up 23.35% as attackers diversify targets
- North Korean groups leading with sophisticated campaigns
The trend is clear: as exchange security improves, attackers target the supply chain - the vendors, partners, and third-party services exchanges depend on.
Supply chain attacks seem to be the new normal
What exchanges secure:
- Private keys ✅
- Smart contracts ✅
- Internal systems ✅
- Employee access ✅
What often goes unchecked:
- Third-party software updates ❌
- Vendor security practices ❌
- Dependency chain integrity ❌
- Real-time component behavior ❌
Every third-party integration creates a potential attack vector:
- Payment processors
- KYC/AML providers
- Trading engine software
- Wallet management tools
- Monitoring dashboards
Each vendor becomes a potential backdoor if compromised.
Key takeaways from this attack
Supply chain attacks succeed because:
- Trusted vendors bypass security scrutiny
- Third-party code often lacks real-time monitoring
- Compromise detection relies on volume, not behaviour.
- Recovery plans assume direct attacks, not vendor issues
Prevention requires:
- Zero-trust approach to all vendors
- Real-time monitoring of third-party components
- Behavioral analysis beyond volume thresholds
- Supply chain incident response planning
Conclusion
BigONE's $27M loss demonstrates that modern exchange security is only as strong as the weakest vendor in the supply chain. As direct attacks become harder, sophisticated threat actors are targeting the trust relationships that make digital finance possible.
Real-time monitoring must evolve beyond watching for large withdrawals to detecting subtle behavioural changes in operational systems, especially those controlled by third parties.
In 2025's threat landscape, your vendor's security incident becomes your security incident.
At Guardrail, we monitor the entire ecosystem, including third-party component behavior and supply chain anomalies. Contact us to discuss comprehensive supply chain security monitoring for your exchange.

.png)



