Arcadia reported on the exploit on their X post here.
The attacker had gamed circuit breakers the day before, preventing the protocol from auto-pausing during the real exploit.
⏱️ The Gap: 4:05 AM attack starts → 4:25 AM team responds → $3.5M already stolen
vs. Real-time alerts that could have stopped it by 4:07 AM
About Arcadia Finance's existing security mechanism
Arcadia Finance is a liquidity management protocol that helps users rebalance their concentrated liquidity positions automatically. The protocol includes sophisticated safety mechanisms - circuit breakers that pause operations when threats are detected.
But on July 15, 2025, these very safety mechanisms became the attacker's weapon of choice.
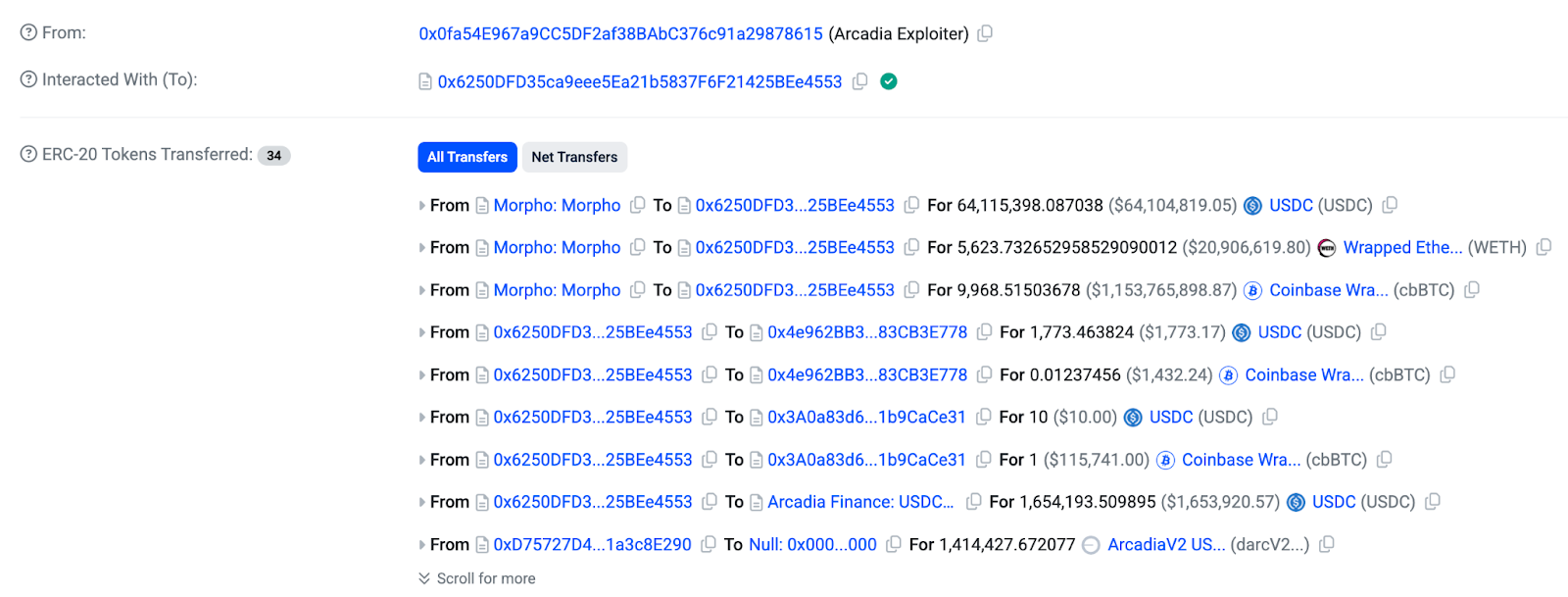
The attacker’s preparation started a day before
This wasn't a typical single-transaction attack. The Arcadia exploit unfolded over two days with surgical precision.
Day 1: setting the trap (July 14)
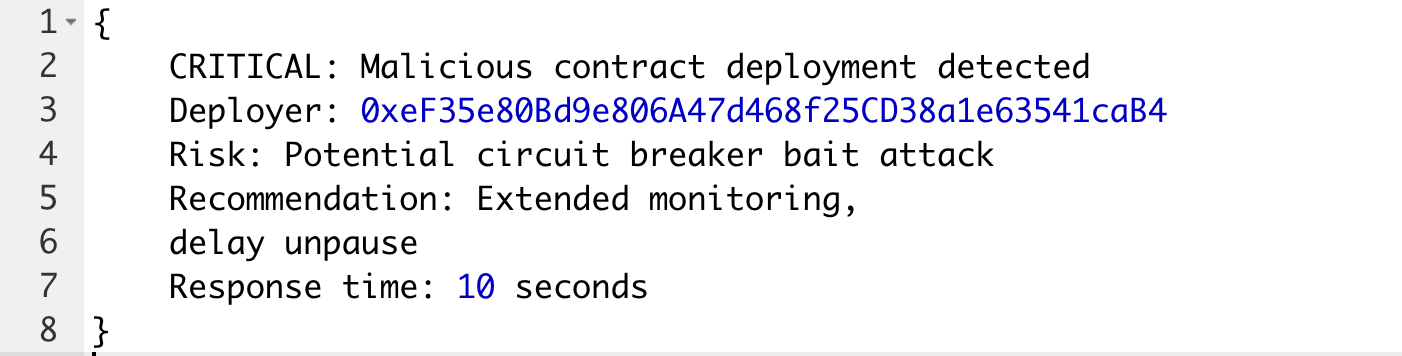
9:22 AM UTC: Attacker deploys malicious contracts via address 0xeF35e80Bd9e806A47d468f25CD38a1e63541caB4
The contracts immediately trigger Arcadia's circuit breakers. The protocol pauses within 10 seconds.
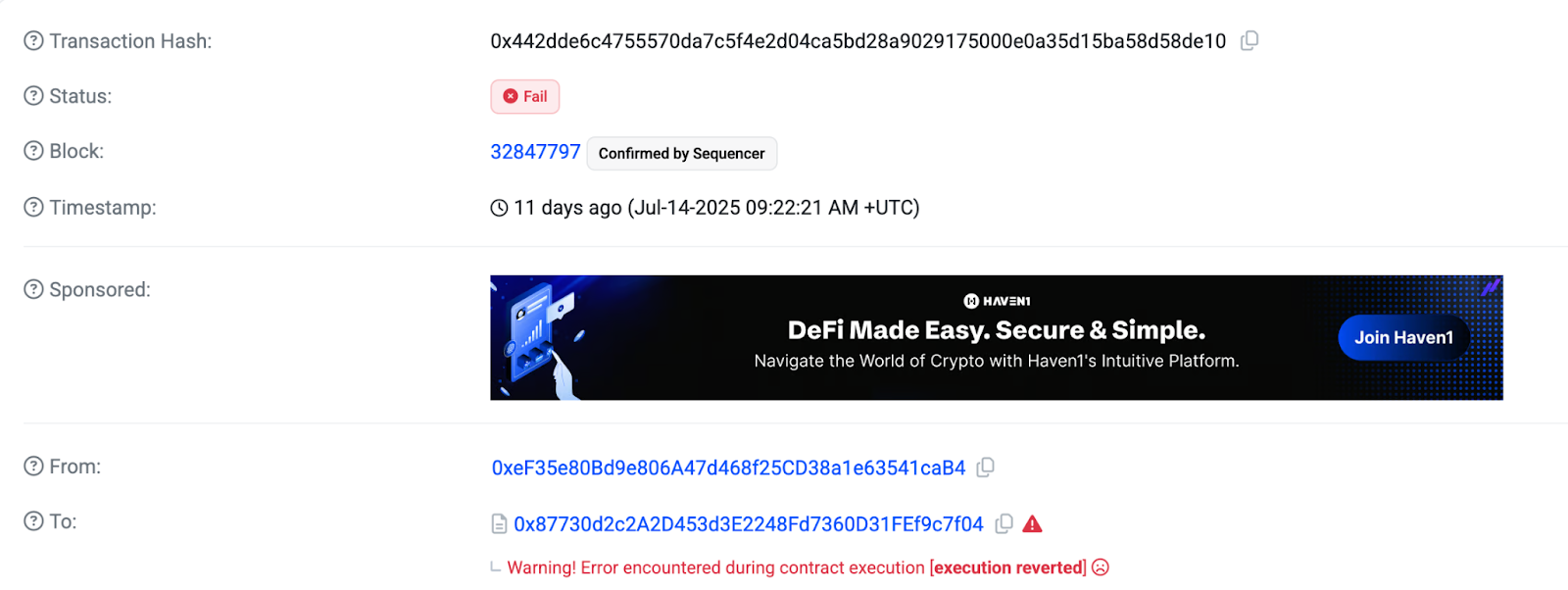
1:05 PM UTC: After 4 hours of analysis, the Arcadia team determines contracts are "suspicious but not harmful" and unpauses the protocol.
Critical mistake: The unpause activated a cooldown period, the protocol's anti-governance-attack mechanism that prevents immediate re-pausing. This meant even if new threats emerged, the protocol couldn't pause again for hours.
Day 2: the real attack (July 15)
4:05 AM UTC: The real attacker (0x0fa54E967a9CC5DF2af38BAbC376c91a29878615) begins the actual exploit.
Circuit breakers trigger again, but due to the cooldown period, the protocol cannot pause. The team watches helplessly as the attack unfolds.
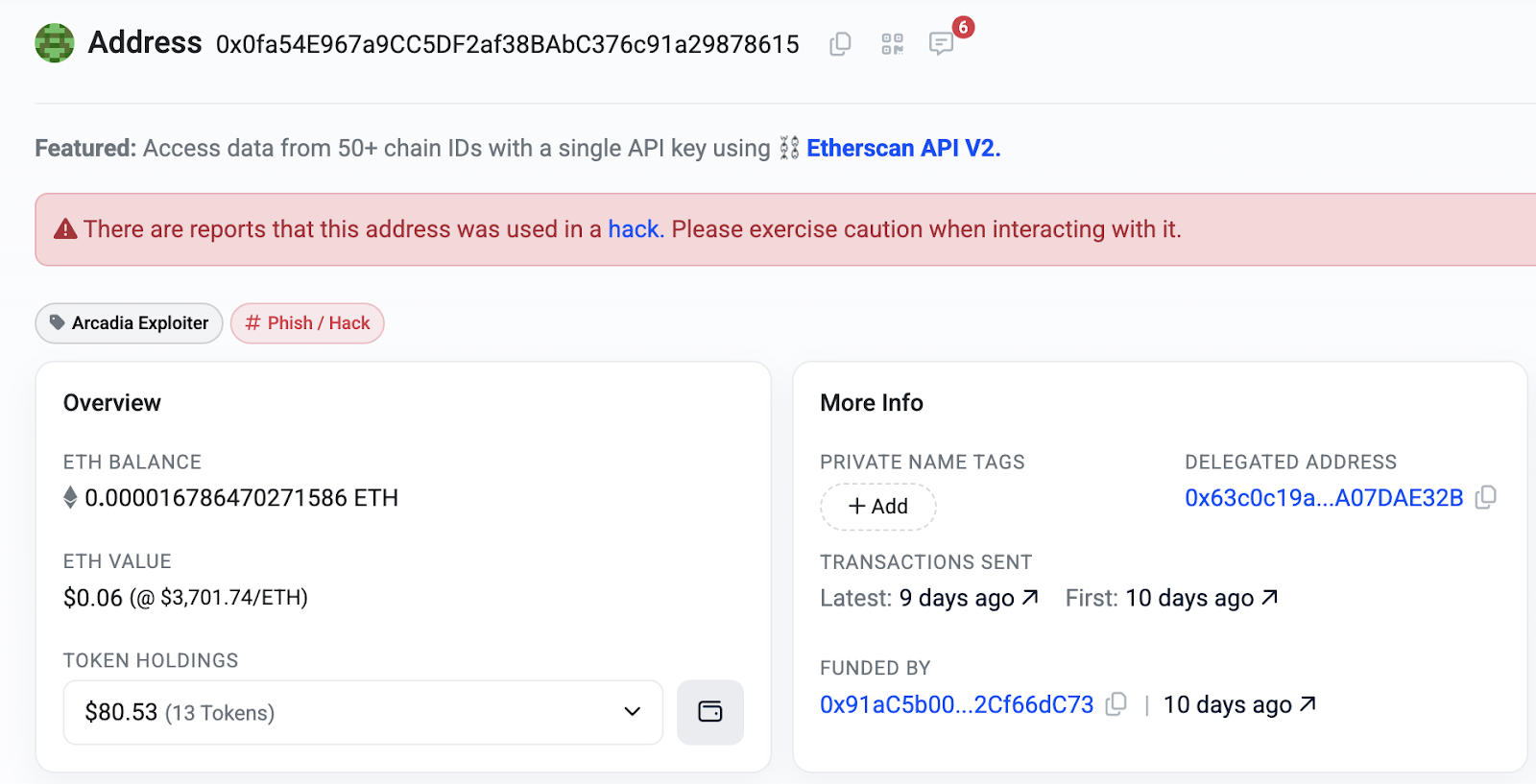
Here’s how the attack was executed
The technical exploit centered on a critical flaw in the SwapLogic._swapViaRouter() function, as it accepted arbitrary router addresses without validation.
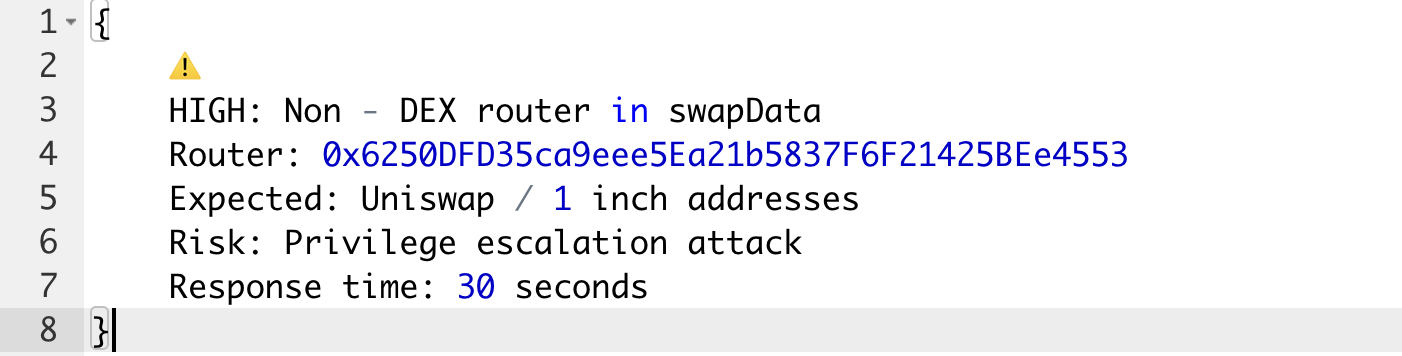
Step 1: The attacker first took flash loan & did account setup
- Borrowed $1.5 billion from Morpho Blue
- Created multiple Arcadia Accounts as attack base
Step 2: Through repay, health checks were bypassed
- Repaid all debt on victim accounts using flash loan funds
- Made accounts "healthy" to bypass failsafes
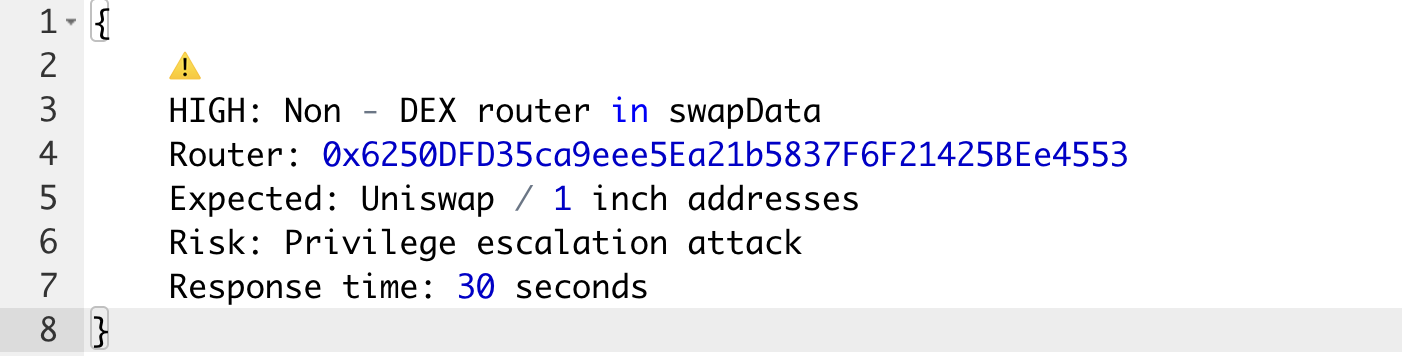
Step 3: Changed the router address via injection
- Called rebalance() function with malicious swapData
- Injected own contract address as the "router"
- When router.call(data) executed, attacker's contract inherited Rebalancer's privileges
Step 4: Access control were bypassed
The malicious router, now calling with msg.sender == Rebalancer, could:
- Access any account that whitelisted the Rebalancer
- Withdraw LP tokens as if it were a trusted asset manager
- Bypass all access controls
Step 5: Drainage of funds from victim’s account
- Withdrew LP positions from victim accounts
- Decomposed liquidity to extract underlying tokens
- Repaid flash loans and kept $3.5M profit
What was the smart contract vulnerability then?
The root issue was in SwapLogic._swapViaRouter():
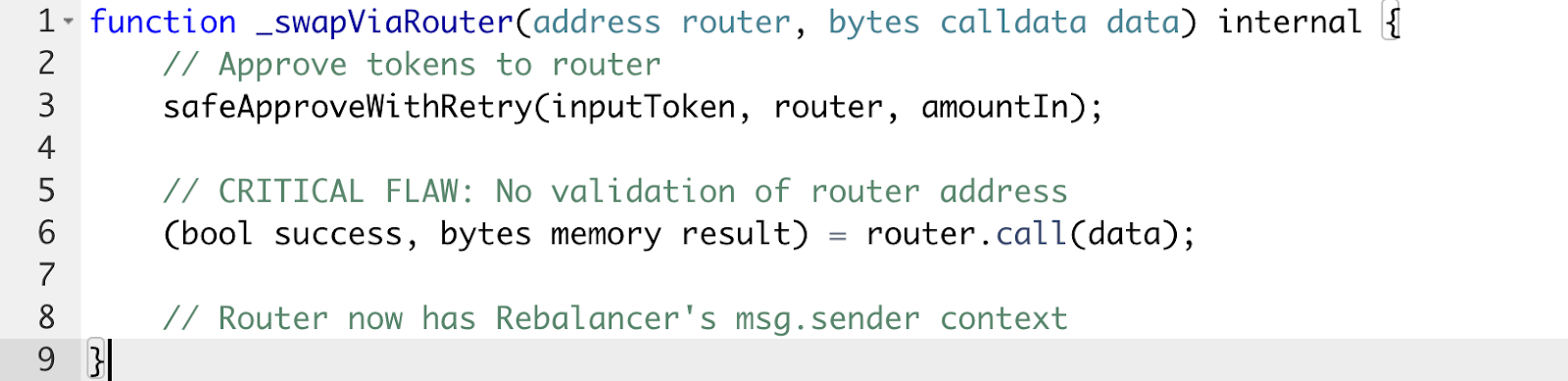
The assumption: router would always be a legitimate DEX (Uniswap, 1inch)
The reality: the attacker registered their own contract as both the router AND the whitelisted Arcadia account.
How could real-time monitoring have prevented this issue from happening?
Alert #1: Suspicious contract deployment (July 14, 9:22 AM)
Alert #2: Unusual router registration (July 15, 4:05 AM)
Alert #3: Massive flash loan + debt repayment (July 15, 4:05 AM)
TL;DR on what actually happened:
❌ 20-minute delay before team notification (4:05 AM attack → 4:25 AM response)
❌ Circuit breakers disabled due to cooldown from day before
❌ No router address validation in real-time
❌ $3.5M drained while team was unaware
The difference when having real-time monitoring turned on:
✅ 30-second alert on malicious router injection
✅ 2-minute response to block suspicious transactions
✅ Attack stopped by 4:07 AM - before any funds lost
✅ $3.5M saved through instant detection
The lesson: safety mechanisms can act as attack vectors
Arcadia's exploit teaches a crucial lesson: security mechanisms can become vulnerabilities if not properly designed. The cooldown period intended to prevent governance attacks became the attacker's shield against emergency responses.
Other protocols with similar risks:
- Any system with pause/unpause cooldowns
- Protocols relying on governance delays for security
- Systems where safety mechanisms can be gamed
Prevention measures from such attacks
- Real-time monitoring of suspicious patterns
- Proper input validation for all external addresses
- Context separation for privileged operations
- Resilient safety mechanisms that can't be gamed
Conclusion
The Arcadia Finance exploit demonstrates how sophisticated attackers exploit not just code vulnerabilities but entire system designs. A two-day attack that turned safety mechanisms into weapons cost users $3.5M.
Real-time monitoring isn't just about catching attacks in progress - it's about recognizing attack preparation and preventing the setup phase entirely.
At Guardrail, we monitor for complex attack patterns, including circuit breaker gaming and privilege escalation attempts. Contact us to discuss comprehensive real-time security for your protocol.